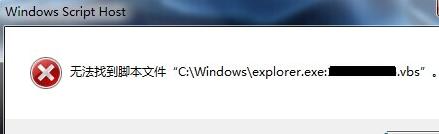
好久没写过杀毒的文章了,也好久没见过vbs病毒了。本例来源论坛求助,问题并不大,应该也是通过U盘中的毒(好久没听到U盘中毒了),然后感染到电脑上,再然后估计是电脑上的杀毒软件杀掉了传染上来的病毒文件,所以在双击桌面上的“计算机”图标无法打开,跳出如下的提示:“无法找到脚本文件‘C:\Windows\explorer.exe:******.vbs’”,这******是一串随机的数字,在win7/8叫“计算机”,如果是XP,就是“我的电脑”,同样是双击无法打开“我的电脑”图标,这个在网上搜索一下,很容易找到类似的问题,都是病毒感染电脑后篡改了注册表中有关“我的电脑”或“计算机”桌面图标设置信息的结果,只有在vbs病毒文件被杀掉的情况下,才会出现提示说找不到脚本文件,否则就会在你双击后运行病毒脚本,而这样就没有提示框弹出了,所以出现提示其实是表示你还算幸运。
首先是防毒,小心U盘感染,太老的话题,不想说。杀毒也不多说,U盘病毒、autorun.inf都不是新鲜的东西,具体问题也要具体分析,至少对于出现弹出找不到脚本文件的提示来说,一般杀毒软件还是能够胜任杀毒工作的,只是不负责修复。所以主要说说修复。
修复就是进入注册表,最简单与保险的方法就是搜索注册表中有关那个vbs文件的关键词。找到后不要直接删掉,估计找到的全部内容的是C:\Windows\explorer.exe:******.vbs,可能只能删除包括冒号在内的后面vbs文件名部分,即保留C:\Windows\explorer.exe,这样比较保险。但是,如果前面有WScript,不知道会不会还是会出错?所以更妥当的是对照其它电脑上看看这里原来是什么样的,照原样修复。
一般来说xp还是win7/8都是在HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D},这是管理桌面上的计算机或我的电脑图标的注册表项,默认情况下shell是没有open在底下的,shell的值也是none的,还真没有explorer.exe。也不能保证只有此一处,最好要搜索全部注册表检查一遍,另外搜索时别选上“全字匹配”的选项,那样可能就找不到了。
这里贴出win7(适用32位、64位)的相关注册值,可以做成reg文件双击导入注册表,至于xp的,网上也有,当然也可以从其它同系统的电脑上导出:
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}]
@="Computer"
"InfoTip"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\
6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\
00,73,00,68,00,65,00,6c,00,6c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,2c,00,\
2d,00,32,00,32,00,39,00,31,00,33,00,00,00
"LocalizedString"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,\
6f,00,6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,\
00,5c,00,73,00,68,00,65,00,6c,00,6c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,\
2c,00,2d,00,39,00,32,00,31,00,36,00,00,00
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\DefaultIcon]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,69,00,6d,00,\
61,00,67,00,65,00,72,00,65,00,73,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,31,\
00,30,00,39,00,00,00
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,73,00,68,00,\
65,00,6c,00,6c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell]
@="none"
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\find]
@=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\
00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,73,00,\
68,00,65,00,6c,00,6c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,00,38,\
00,35,00,30,00,33,00,00,00
"LegacyDisable"=""
"SuppressionPolicy"=dword:00000080
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\find\command]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,45,00,78,00,70,00,6c,00,6f,00,72,00,65,00,72,00,2e,00,65,00,78,00,\
65,00,00,00
"DelegateExecute"="{a015411a-f97d-4ef3-8425-8a38d022aebc}"
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Manage]
@=hex(2):40,00,25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,00,6f,00,74,\
00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,6d,00,\
79,00,63,00,6f,00,6d,00,70,00,75,00,74,00,2e,00,64,00,6c,00,6c,00,2c,00,2d,\
00,34,00,30,00,30,00,00,00
"MUIVerb"=hex(2):40,00,25,00,73,00,79,00,73,00,74,00,65,00,6d,00,72,00,6f,00,\
6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\
00,6d,00,79,00,63,00,6f,00,6d,00,70,00,75,00,74,00,2e,00,64,00,6c,00,6c,00,\
2c,00,2d,00,34,00,30,00,30,00,00,00
"SuppressionPolicy"=dword:4000003c
"HasLUAShield"=""
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\shell\Manage\command]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,43,00,6f,00,\
6d,00,70,00,4d,00,67,00,6d,00,74,00,4c,00,61,00,75,00,6e,00,63,00,68,00,65,\
00,72,00,2e,00,65,00,78,00,65,00,00,00
[HKEY_CLASSES_ROOT\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\ShellFolder]
"HideOnDesktopPerUser"=""
"PinToNameSpaceTree"=""
>> 除非说明均为原创,如转载请注明来源于http://www.stormcn.cn/post/1594.html

