某日突然发现XP系统的搜索突然不能用,打开搜索,窗口标题上不象以前那样显示“搜索结果”四个字,而且搜索任何文件名真的都不会显示结果出来,右边的框里永远是空白的。
试了网上说的两个方法:1、运行命令重注册文件:regsvr32 vbscript.dl、regsvr32 jscript.dll和regsvr32 mshtml.dll;2、重装搜索组件:进入C:\Windows\inf文件夹,右键单击srchasst.inf文件,选择“安装”菜单,插入Windows XP安装光盘,重新安装Windows XP的搜索服务组件,都无效果,没有修复搜索功能。
拖延日久,偶然间在另一台电脑上的注册表中搜索对照,竟然发现原来是某篡改IE主页的东东所害,删除恢复被破坏的注册表项后,终于恢复搜索组件,特此记录如下。
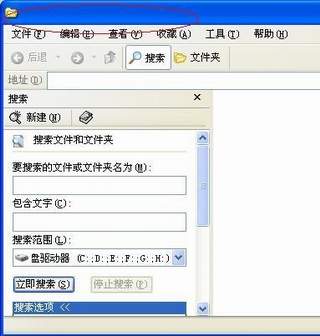
故障时的搜索窗口
以下是被篡改的注册表项(注意颜色部分,可与后面正常的注册表项与值对比,红色是新添加的,注意那个网址):
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}]
@="Internet Explorer"
"LocalizedString"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,\
6f,00,6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,\
00,5c,00,53,00,48,00,45,00,4c,00,4c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,\
2c,00,2d,00,33,00,30,00,35,00,32,00,30,00,00,00
"IntroText"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\
6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\
00,53,00,48,00,45,00,4c,00,4c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,2c,00,\
2d,00,33,00,31,00,37,00,35,00,34,00,00,00
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\DefaultIcon]
@="C:\\Program Files\\Internet Explorer\\iexplore.exe"
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,53,00,48,00,\
45,00,4c,00,4c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\shell]
@="打开主页(&H)"
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\shell\属性(&R)]
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\shell\属性(&R)\Command]
@="Rundll32.exe Shell32.dll,Control_RunDLL Inetcpl.cpl"
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\shell\打开主页(&H)]
@=""
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\shell\打开主页(&H)\Command]
@="C:\\Program Files\\Internet Explorer\\MUI\\iexplore.exe %1 http://www.97199.com/?k1/"
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\ShellFolder]
"Attributes"=dword:00100000
@="HideOnDesktopPerUser"
正常时的注册表项与正常值:
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}]
@="Search Results Folder"
"LocalizedString"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,\
6f,00,6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,\
00,5c,00,53,00,48,00,45,00,4c,00,4c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,\
2c,00,2d,00,33,00,30,00,35,00,32,00,30,00,00,00
"IntroText"=hex(2):40,00,25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,\
6f,00,74,00,25,00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,\
00,53,00,48,00,45,00,4c,00,4c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,2c,00,\
2d,00,33,00,31,00,37,00,35,00,34,00,00,00
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\DefaultIcon]
@="%systemroot%\\system32\\shell32.dll,-134"
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\InProcServer32]
@=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,00,25,\
00,5c,00,73,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,53,00,48,00,\
45,00,4c,00,4c,00,33,00,32,00,2e,00,64,00,6c,00,6c,00,00,00
"ThreadingModel"="Apartment"
[HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\ShellFolder]
"Attributes"=dword:20180000
@=""
这个{e17d4fc0-5564-11d1-83f2-00a0c90dc849},其实是这里引用(可参考关于桌面多出的IE图标的说明中的“NameSpace”一段):
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Desktop\NameSpace\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}]
@="Search Results Folder"
其实篡改者在上面HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\shell\打开主页(&H)\Command加入网址的本意是使中招用户在打开系统搜索时就打开他要推广的网页(似乎是之前某次试验某软件时中的,没有清理干净),但在我的电脑上却没有出现这种效果,只是出现前文所说的空白搜索结果的情形,不知道是为什么。
找到原因,修复就简单了,根据正常项目删除新加的HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}\shell\,其余的被修改部分,按原样恢复。另外,还有一处:HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849},也有被篡改的情况,不过在HKEY_CLASSES_ROOT\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}修改完成后刷新一下,HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{e17d4fc0-5564-11d1-83f2-00a0c90dc849}也就正常了,当然建议再去检查下,没有正常再改不迟。
>> 除非说明均为原创,如转载请注明来源于http://www.stormcn.cn/post/756.html

